Enhancing Threat Detection with JA3 in Cybersecurity
Introduction
As the frequency of DDoS attacks has been on the rise in recent years, along with their growing complexity, it becomes increasingly crucial to explore more effective methods for identifying malicious requests targeting web servers.
According to CloudFlare’s report, despite a year-long decline, the final quarter of the year witnessed a significant 79% surge in HTTP DDoS attack traffic.
Overview
To keep it short JA3 is a method for fingerprinting clients. It is a technique that can be used to identify malicious traffic and detect malware.
What is TLS ?
In order to understand JA3 it is crucial to understand what TLS is. TLS stands for Transport Layer Security and is a cryptographic protocol that provides end-to-end security of data sent between applications over the Internet. It is the successor of SSL (Secure Sockets Layer) and is used to encrypt the data sent between a client and a server. TLS is used in many applications such as web browsing, email, instant messaging, and voice over IP.
Maybe a diagram here ?
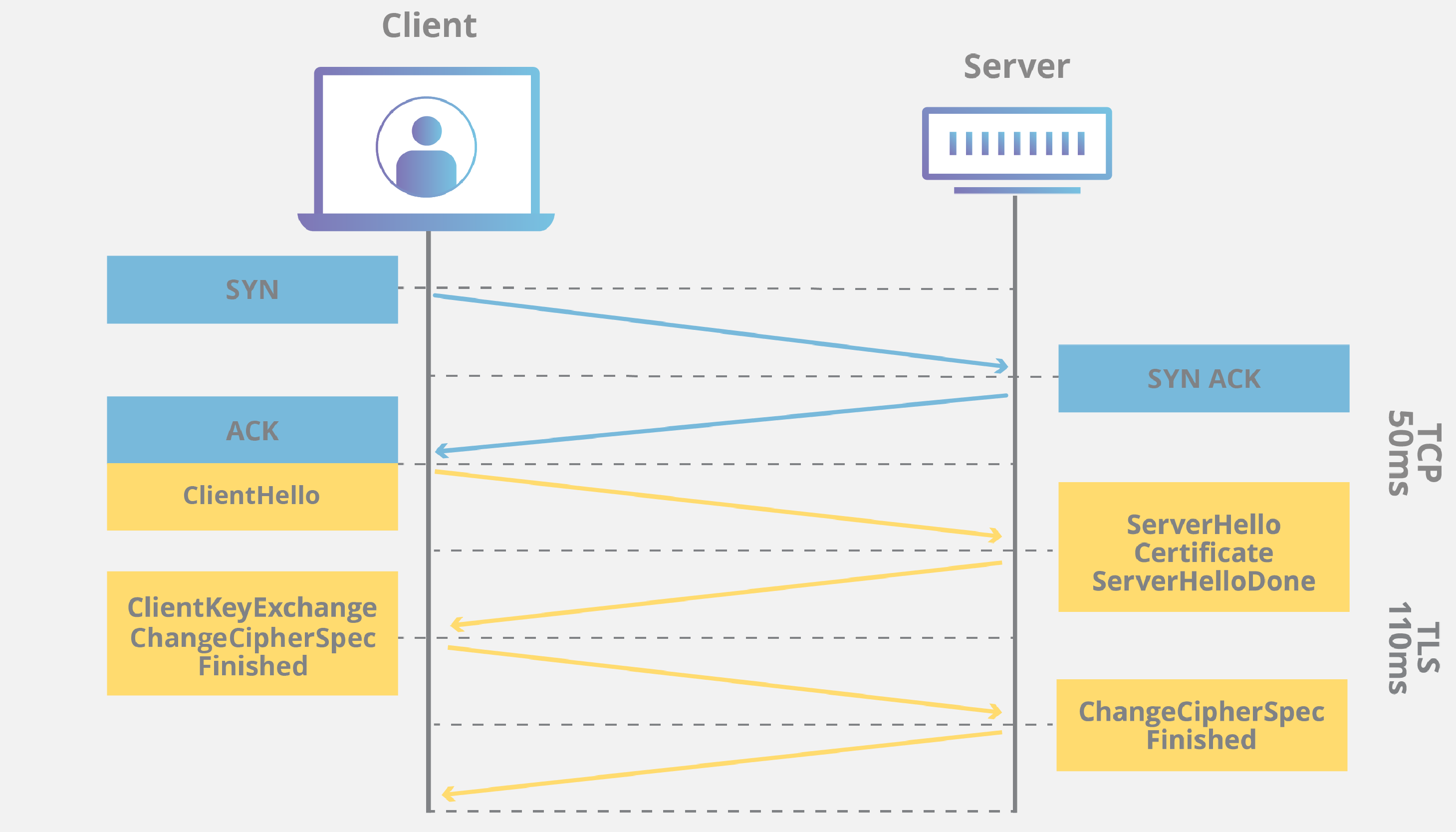
All you need to understand is that at one point the Client sends a Client Hello packet to the server. The content of this packet can be used to calculate a JA3 fingerprint and therefore possibly identify the client.
What is a JA3 : in depth ?
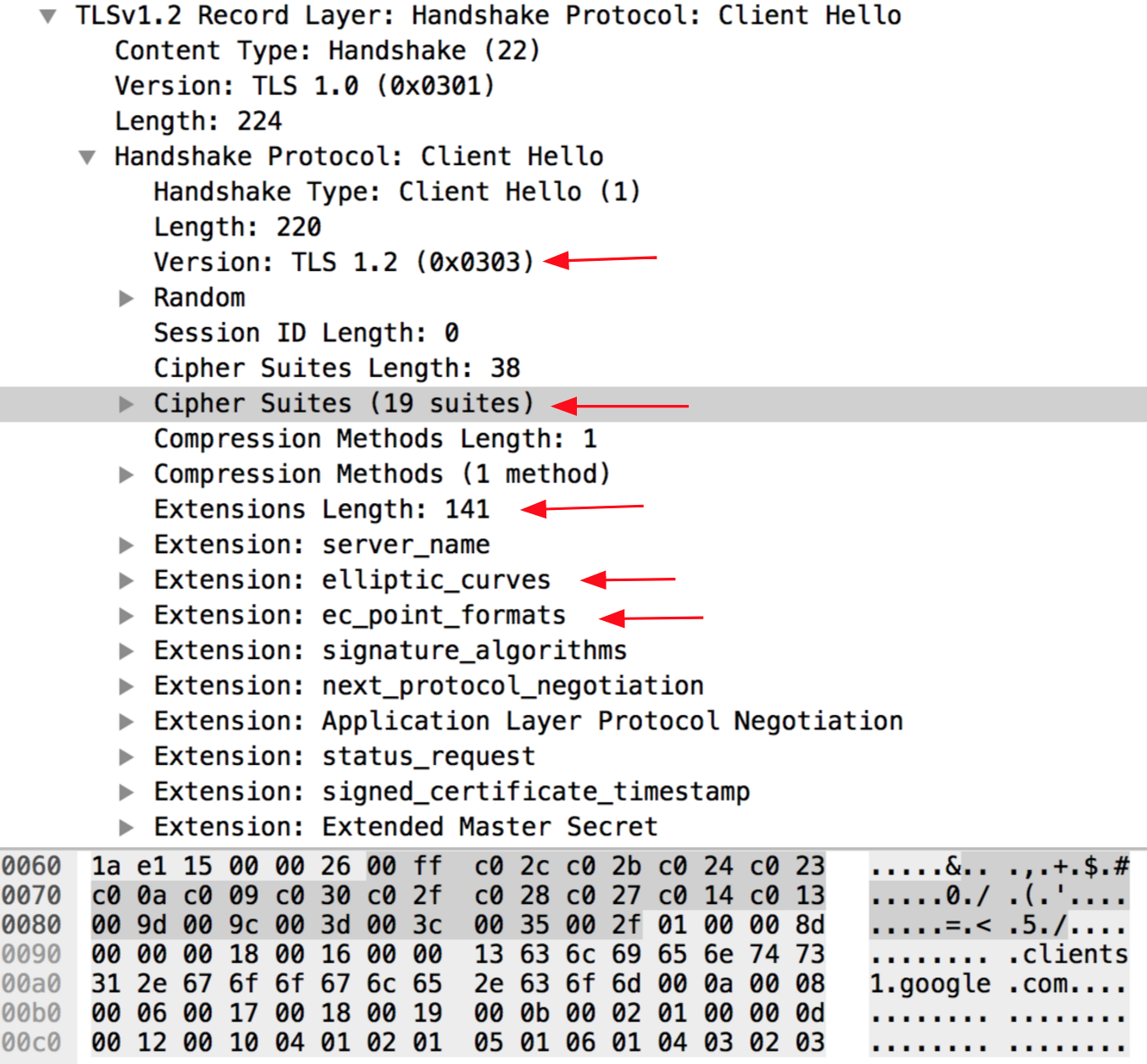
To keep it simple, the client hello packet contains a list of supported ciphers aswell as the TLS version, extensions, elliptic curves and Point Formats. The server will then choose one of the ciphers and elliptic curves from the list and send it back to the client in the Server Hello packet.
The field order is as follows:
TLSVersion,Ciphers,Extensions,EllipticCurves,EllipticCurvePointFormats
This particular order is important because it is used to calculate the JA3 fingerprint.
In our example the JA3 fingerprint would be: 769,47–53–5–10–49161–49162–49171–49172–50–56–19–4,0–10–11,23–24–25,0
And then hashed with MD5 to get the final fingerprint:
ada70206e40642a3e4461f35503241d5
Note that modern browsers randomize the order of the ciphers and elliptic curves in the Client Hello packet but many malware samples do not, And therefor many clients can be identified by their JA3 fingerprint.
A little example
Here is a website that returns the JA3 fingerprint aswell as many infos on the client that connects to it.
The website returned the following JA3 signature for my Browser:
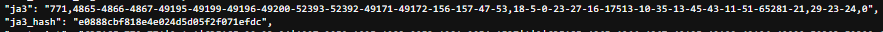
And after refreshing the page the signature changed
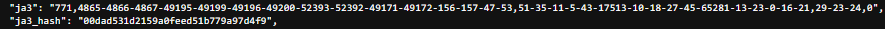
Testing with Python and using the requests library to send a request to the website:
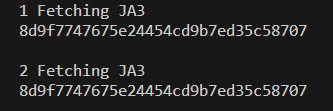
We can see that the JA3 fingerprint didn’t change making it possible to identify the client.
Here is the source code of the script: Repo
How can JA3 be used in Cybersecurity ?
Now, knowing that certain clients can be identified by their JA3 fingerprint, it is possible to use this technique to detect malware and malicious traffic.
For example, if a client is sending a lot of requests to a server and the server detects that the JA3 fingerprint of the client is the same as the one of a known malware, it is possible to block the client.
Some databases have even emerged to store JA3 fingerprints of known malware and malicious traffic like ja3.zone for example.
Conclusion
To conclude, JA3 is a technique that can be used to identify clients and detect malware. It is a very effective method for detecting malicious traffic and can be used to enhance threat detection in Cybersecurity. Many companies such as CloudFlare, Datadome are already using JA3 to detect malware and malicious traffic and it is a technique that will be used more and more in the future.
In order to protect yourself against CyberThreats it is important to be aware of the latest techniques and to keep yourself informed on the latest news in Cybersecurity.
Thank you for reading this article, I hope you enjoyed it and learned something new. Feel free to contact me if you have any questions or suggestions.
Sources
- https://blog.cloudflare.com/ddos-threat-report-2022-q4/
- https://engineering.salesforce.com/tls-fingerprinting-with-ja3-and-ja3s-247362855967/
- https://www.codecademy.com/resources/blog/what-is-hashing/
- https://www.simplilearn.com/tutorials/cyber-security-tutorial/md5-algorithm
- https://engineering.salesforce.com/wp-content/uploads/2022/04/0_zZFKcFS-CkMtjUw1.png
- https://cf-assets.www.cloudflare.com/slt3lc6tev37/5aYOr5erfyNBq20X5djTco/3c859532c91f25d961b2884bf521c1eb/tls-ssl-handshake.png
- https://tls.peet.ws/api/all